Steppa provides a large-scale of cyber intel and security products and services that fit in the following areas: risk management, technology legal advice, security operation center (SOC), security data sharing and threat Intel, research and development (R&D), cyber security consulting as a service, training and education, among others.
Our services and products are available 24/7. Contact us now if you need to build your own capability or for any further information. We will get back to you within 24 hours.
-

Digital Forensics and Investigations
Digital Forensics & Investigations in UAE and MENA Protect your organization from cyber threats and internal risks with our expert…
-

Malware, Ransomware and Rootkit Removal
Why Malware, Ransomware and Rootkit Removal? Ransomware, Advanced Persistent Threats (APTs), and other malware are still the most common cyber-attacks…
-
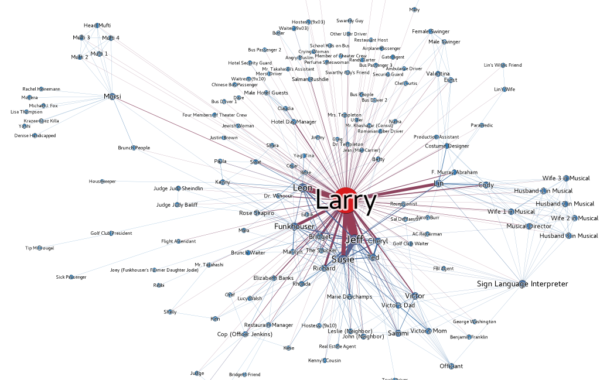
Public Discovery
Why Public Discovery for Intelligence Gathering? Hackers use the Internet to identify vulnerabilities or even to publish sensitive information about…
-
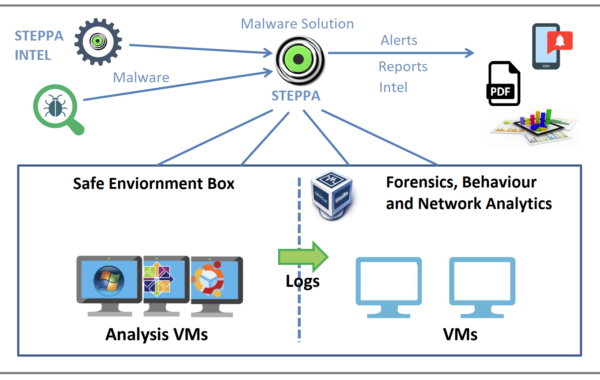
Malware Analysis Solution
Why Malware Analysis Solution? Malware is still the number one threat to Cyber Security. As such, Steppa malware analysis solution…
-

Social Media Intelligence
Social Media Analytics for Business Intelligence, Brand and Identify Protection. This service is for business, celebrities, bloggers, media, sales, marketing…
-
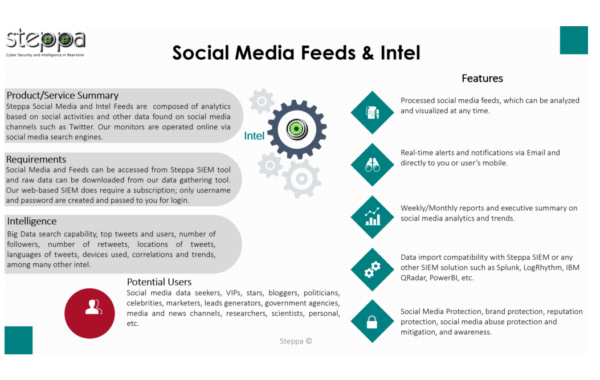
Social Media Feeds & Analytics
The term "social media intelligence" (SMI) refers to a group of tools and services. The latter enable businesses to respond…
-

IT Audit and Compliance
Steppa IT auditors allow your business to be compliant with national and international standards.
-

Steppa SIEM
Leverage steppa SIEM (Security Information and Event Management) to visualize, infer, analyze and respond to cyber activities in real-time.
-
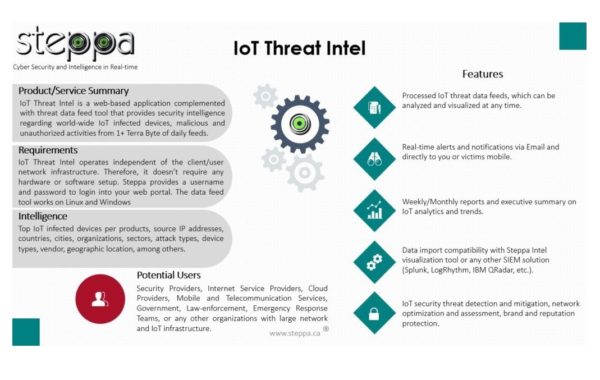
IoT Intelligence – Threat Intel
Why IoT intelligence? In fact, as per experts, there will be 41 billion Internet of Things (IoT) devices by 2027. …
-
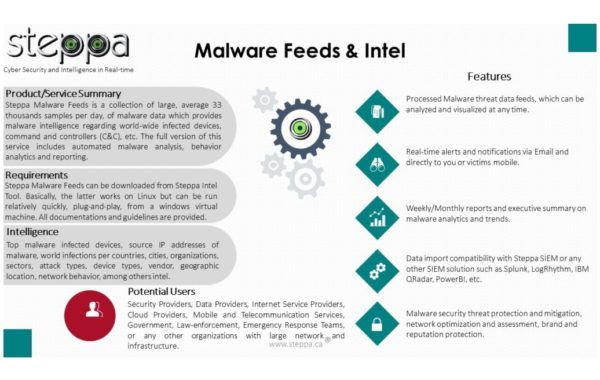
Malware Threat Intel – Datasets
Malware Threat Intel is a web-based application complemented with malware sample feeds provided via Steppa Intel tool. Furthermore, the tool…
-
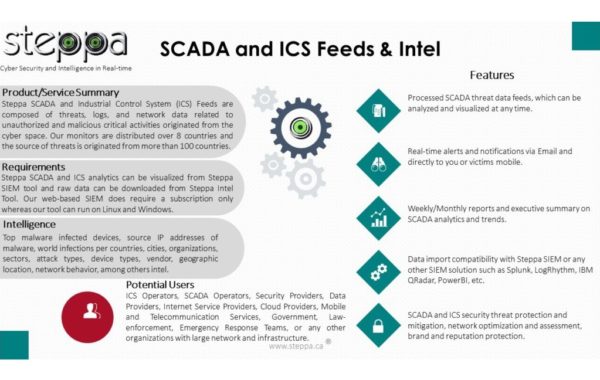
SCADA Threat Intel – Datasets
This data contains suspicious and malicious OT cyber activities against SCADA and Industrial Control Systems. Such systems operate in the…
-

Steppa Detection and Prevention
Real-time and automated detection and prevention of intrusions, malware, scans, DDoS and other threats against servers, websites, and critical assets…
-

Vulnerability Assessment and Pentest
Why Vulnerability Assessment and Pentest? Vulnerability Assessment and Pentest (penetration testing) are probably the most used security evaluation techniques. Because…
-

Research and Development (R&D)
Allow our data scientists and engineers at steppa to build innovative solutions for your business
-
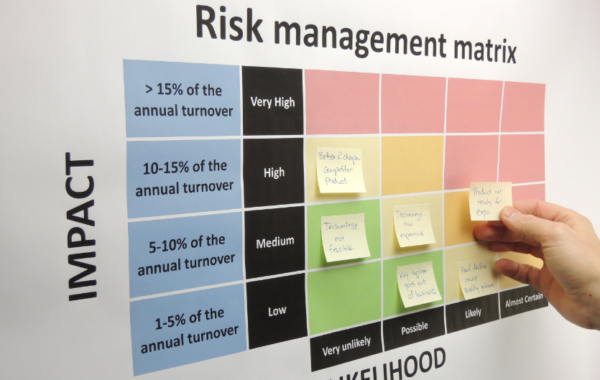
Risk Management Tool
Assess and prepare your business against cyber security threats and attacks
-

Managed Services
Focus on your business, allow steppa to take care of your security concerns
-

Cyber Security Consulting
Why cyber security consulting service at Steppa? Steppa cyber security consulting service can help you develop your own capability. Furthermore,…


















